The fire at the OVH data center (French number 1 in cloud computing) in March 2021, which affected 3.5 million websites, brought to light the usefulness of having an advanced backup policy. But this is not the only danger that can impact a website, there are also computer attacks, hacking, bugs, malicious acts, etc.
PhDev Informatique maintains and monitors several Internet platforms containing sensitive customer data. This is why we have implemented a data backup strategy at several levels.
Various dangers
What dangers could threaten our platforms? We can classify them into 3 categories.
Hardware failure
We may be “in the cloud”, but at the end of the chain there’s still a “real” machine. In our case, a computer behind a multitude of network intermediaries, cables and fibers. Despite the quality of all this hardware, failure is always possible, as in the example described in the introduction to this article.

Accidental deletion
It can happen that a user deletes or modifies important information by mistake. When this happens, we need to be able to go back in time to find all the details of this information.

Malicious intent
An identified user will delete data or enter false information to harm the company.
The hacker will seek entry to the computer system to delete, recover or encrypt the database in order to harm, resell information or demand ransom.

Solutions
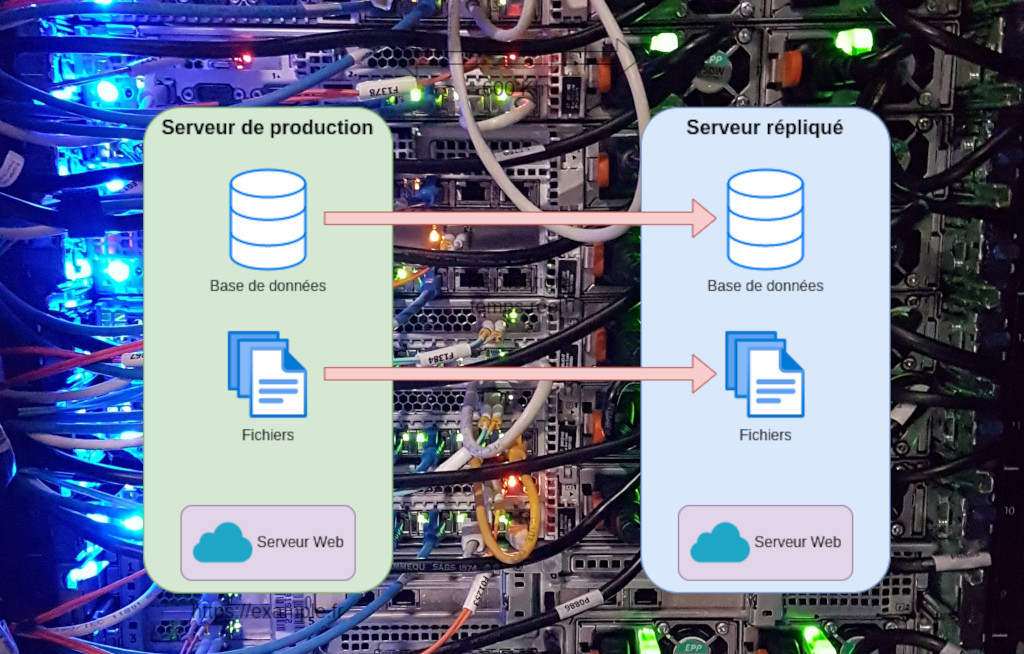
Real-time synchronization
When this solution is implemented, all platform activities are replicated in real time to another identical server, geographically remote. In the event of failure of the main server, the domain (https://example.fr) is simply redirected to the replicated server. This operation causes a momentary interruption in service, but no data is lost.
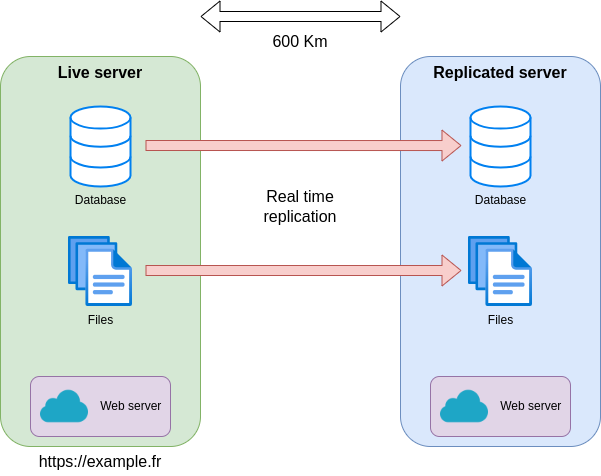
Daily backups / rotation
The most natural and easy to set up is the daily backup of databases and files. In the event of accidental deletion of data, an old backup can be reloaded on a test platform. Obviously, this backup must be made on another server (I’ve seen servers where backups were kept locally).
We keep multiple backup versions, with a rotation strategy that allows us to retrieve backups that are more than a year old. The frequency of backups kept is one per day for the last week, one per month for the last year, etc …

Anti-hacking measures
It is the job of the “computer scientist” to protect his platform as much as possible by rigorously applying a few principles:
- Keep abreast of technological developments
- Keep software up to date, avoid unnecessary software
- Our servers run exclusively on Linux, a proven open-source operating system.
- Ports must be protected: firewall, if possible avoid standard port numbers (ssh, mysql, …).
- Protection against DDoS and brute force attacks (FailToBan)
- Use of advanced framework to avoid SQL insertion, MitM and XSS attacks
- Frequent backups, including some on non-connected media.
- Partition user accounts, use temporary keys for outgoing documents.
- Constant monitoring of servers: abnormal activity, resources not saturated.
User rigor
The main danger is posed by users. Even if our systems require a relatively complex password, there are still risky behaviors, some of which I’ve already seen:
- Write your password on a PostIt stuck to the screen
- Left your session open
- Password based on date of birth, children’s first names, dog’s name, etc.
- Save passwords in your browser
We can also mention more advanced hacking via users, such as :
Key logger software: a small program records all your keystrokes and transmits them to a third party. As you are required to enter your login and password, the malicious person can retrieve them.
Hardware key logger: can take the form of a small USB key or cable, or can be mounted in your computer, or connected via WiFi: like the previous one, it records all your keystrokes.
Camera: There are some very discreet ones with very good resolutions: they can film you typing your password. By replaying the recording in slow motion, your password can be recovered.
To counter the last three dangers, there’s only the user’s attention, changing the password often enough or double identification.